Ever wondered if your browsing habits are being tracked even when you think they’re private? It’s a valid concern—because while that private browsing switch might promise invisibility, many users don’t realize the limits (and loopholes) of this feature. Spoiler alert: “Private” doesn’t always mean *private*. But before we dive in, here’s some good news—you can take control of what data is shared and learn to use tools like monitoring kill switches effectively.
In this article, you’ll discover:
- Why “incognito mode” isn’t enough.
- A step-by-step guide on using private browsing alongside advanced privacy measures.
- Tips to improve your online security without losing your sanity.
Table of Contents
- The Truth About Private Browsing
- How to Leverage the Private Browsing Switch + Monitoring Kill Switch
- Top Tips for Securing Your Online Activity
- Real-Life Use Cases of Enhanced Privacy Tools
- Frequently Asked Questions About Private Browsing
Key Takeaways
- Private browsing only hides activity locally—it won’t stop trackers or ISPs from seeing your moves.
- A monitoring kill switch acts as a fail-safe for leaks during encrypted sessions.
- Pairing the private browsing switch with additional safeguards ensures better anonymity.
What’s Wrong With Using Just a Private Browsing Switch?
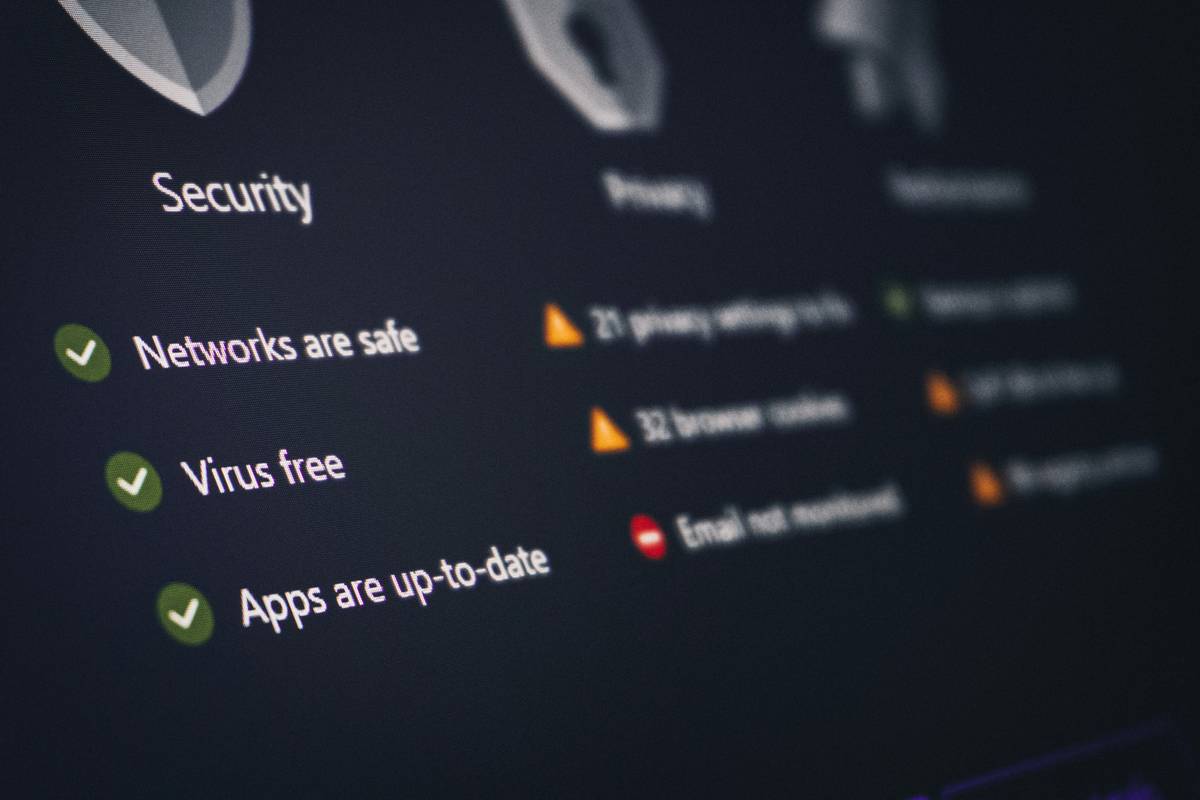
Let’s talk about my epic fail: I once spent an entire week thinking I was safely hiding my tech research by switching to incognito mode. Then I Googled something innocuous… and BAM! Ads for it started appearing everywhere. Turns out, websites, browsers, and Internet Service Providers (ISPs) could still see everything.
Here’s the tea: A private browsing switch (like Chrome’s Incognito Mode or Firefox’s Private Window) clears your local history after the session—but it does ZERO to block external entities from snooping. The key problem lies in false peace of mind. While your device may feel clean, your digital footprints remain exposed.
How to Use the Private Browsing Switch PLUS Monitoring Kill Switch

Optimist You: “I’ve got this! Privacy secured!”
Grumpy You: “Hold up—we need layers of protection.”
Step 1: Enable Private Browsing
First things first—activate the built-in private browsing function in your preferred browser:
- Open your browser settings menu.
- Select “New Private Window” or equivalent.
- Confirm no logs will be saved post-session.
Step 2: Add a VPN for Better Security
This is where you level up. Download a reputable virtual private network (VPN), which encrypts your traffic and masks your IP address. Make sure it has a high-quality monitoring kill switch!
Step 3: Enable the Monitoring Kill Switch
The monitoring kill switch is like the deadbolt on your front door. If the connection drops unexpectedly, the kill switch stops all outgoing traffic until encryption resumes. To enable:
- Go to your VPN app’s settings.
- Locate the “Kill Switch” toggle and activate it.
Best Practices for Maximizing Your Private Browsing Experience

- Don’t Trust Cookies Alone: Clear cookies regularly and opt out of third-party trackers manually.
- Use HTTPS Sites: Always look for URLs starting with https:// instead of http:// —it adds another layer of encryption.
- Avoid Terrible Advice Like This One: Thinking installing random “privacy” extensions makes you untouchable. Many are scams or worse—they steal more info than you’d imagine.
When Did These Strategies Save the Day?
Consider Jane Doe, who needed secure browsing for remote work tasks involving sensitive client data. By combining her private browsing switch with a top-tier VPN and its monitoring kill switch, she avoided corporate surveillance software embedded in public Wi-Fi networks. Her employer praised her proactive approach to maintaining confidentiality.
FAQs: Everything You Need to Know About the Private Browsing Switch
Q1: Does private browsing hide my location?
Nope, unless paired with geo-blocking tools like a VPN or Tor browser.
Q2: Can hackers bypass the private browsing switch?
Hackers generally focus on vulnerabilities elsewhere—not within the switch itself—but they CAN exploit weak passwords or unprotected connections.
Q3: Is there such a thing as TOO much privacy?
Rant moment: Yes, overcomplicating your setup leads to frustration (hello, endless login prompts). Balance simplicity with smart security choices.
Conclusion
So, what now? Hopefully, you understand why relying solely on the private browsing switch leaves gaps—and how complementing it with a monitoring kill switch supercharges your privacy game.
If nothing else sticks today, remember one truth: Your online identity deserves protection, whether through simple tweaks or robust systems. Like Pac-Man chasing pellets, stay vigilant but enjoy the chase!
And just because—a little retro wisdom:
Browser tabs hum late at night, Data trails vanish without fright. Stay private; keep secrets tight.